The number of organization using blog is growing rapidly. Many staff members and volunteers use blogs for conversation, news, and general transparency, it seems like organizations are begin to understand the use of blog. Organizations of all sizes and sectors are utilizing this community building tool.
What is blog? what is the difference between blog and website?
All website has a home page, with links to lots of sub-pages that have more detail. Most business site follows the same format. But a blog is much simpler than a website. A blog is normally a single page of entries. There may be archives of older entries, but the main page of a blog is all anyone really cares about. A blog is organized in reverse chronological order, from most recent entry to least recent. A blog is normally public where the whole world can see it. Basically, a blog is a lot like an online journal or diary. The author can talk about anything and everything. Many blogs are full of interesting links that the author has found. Blogs often contain stories or little snippets of information that are interesting to the author.
What is the advantage of using Blog for organization?
Blogs are cost effective, no need to know programming, easy to update and build up online network.
Cost-Effective Site Creation: There is need to worry about site creation costs and maintenance fees when using free blog sites. This Internet service offers fully-functional site development tools to create professional-looking websites complete with features and applications. No don't have to hire a professional Web developer to do the job since free blog sites can be made with just a few clicks of a mouse button.
No Need For HTML Programming: One problem faced by organization is coming up with a site from scratch using HTML programming. HTML or Hypertext Markup Language is used by Web programmers to create websites complete with all the features and provisos that make it look professional and clean. Free blog sites offer a user-friendly interface that will allow an organization to create their website just by toggling some of its features. There is no need to place in HTML formatting tags instead by just using text boxes, site contents are created. Pictures and Links can be entered just by clicking the button. Blogs are user friendly.
Easy Update: Information is very important in putting up a website. To improve or maintain the online popularity, it is necessary to update information relevant to the topic that will attract the interest of other visitors. Free blog sites contains features where information can be posted just by typing and pasting it. And, third-party applications can be submitted directly to the blog without opening a Web browser. Basically, managing a blog is much easier and efficient than website.
Build Up the Online Network: Since most Web surfers today are busy checking out blogs instead of looking for information they need on different sites on the Internet. Therefore, an organization can easily build-up their online network with every visitor that drops by this page. Since each of the posts can be given a comment by anyone who views the blog, they can easily interact with them to increase their online popularity. Guestbook and chat room are offered free by blog sites to make the page as interactive as possible for better communication with others.
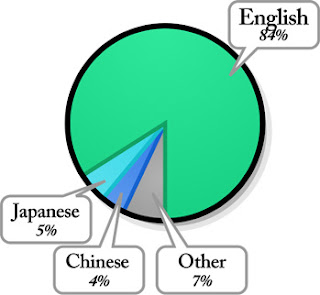
The Chart below shows the percentage of each different topics that are posted in blogs. And different languages that are used in blogs.
Although there are several advantages, many organization avoid using blogs due to some disadvantages that associated with it. For example blogs are easy to start but they are hard to maintain. Writing coherently is one of the most difficult and time consuming tasks for a human being to undertake. Far from blogs being a cheap strategy, they are very expensive one, in that they eat up time. As a result, many blogs are not updated, thus damaging rather than enhancing the reputation of the organization. Also, many people don't have very much to say that's interesting or unable to write down their ideas in a compelling and clear manner. Moreover, organizations are not democracies. The web makes many organizations look like disorganizations, with multiple tones and opinions. Most customer prefers it if the organization they are about to purchase from is at least somewhat coherent.
References:
http://en.wikipedia.org/wiki/HTML
http://www.modernlifeisrubbish.co.uk/article/leading-average-top-blog-trends
http://www.netsquared.org/blog/amysampleward/organizations-putting-blogs-good-use